The Office for Civil Rights (OCR) in the Department of Health and Human Services (HHS) in January published a newsletter concerning cyber threats to entities storing PHI (protected health information), which is covered by the privacy and security rules of the Health Insurance Portability and Accountability Act (HIPAA).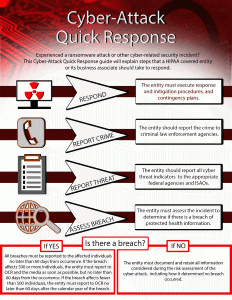
The newsletter begins by nothing that “Organizations that provide necessary services or maintain sensitive data, such as Healthcare and Public Health (HPH) sector organizations are often the targets of cyber extortion attacks. ”
The newsletter also warns that the use of ransomware could render stored data inaccessible, or worse, make it publicly available if a ransom isn’t paid.
Because ransomware denies access to data, maintaining frequent backups and ensuring the ability to recover data from backups is crucial to recovering from a ransomware attack, OCR advises.
The newsletter also offers several suggestions and best practices for thwarting cyber attacks:
• Implementing a robust risk analysis and risk management program that identifies and addresses cyber risks holistically, throughout the entire organization;
• Implementing robust inventory and vulnerability identification processes to ensure accuracy and thoroughness of the risk analysis;
• Training employees to better identify suspicious emails and other messaging technologies that could introduce malicious software into the organization;
• Deploying proactive anti-malware solutions to identify and prevent malicious software intrusions;
• Patching systems to fix known vulnerabilities that could be exploited by attackers or malicious software;
• Hardening internal network defenses and limiting internal network access to deny or slow the lateral movement of an attacker and/or propagation of malicious software;
• Implementing and testing robust contingency and disaster recovery plans to ensure the organization is capable and ready to recover from a cyber-attack;
• Encrypting and backing up sensitive data;
• Implementing robust audit logs and reviewing such logs regularly for suspicious activity; and
• Remaining vigilant for new and emerging cyber threats and vulnerabilities (for example, by receiving US-CERT alerts and participating in information sharing organizations).
